AWS IAM Roles, EC2 Instances to Lambda Functions with Shared Responsibility Model.
Hello there 👽
In this article, we are going to learn about the AWS IAM Roles and the Shared Responsibility model for the IAM.
IAM Roles for service
Some AWS services will need to act on our behalf. To do so, we will assign permission to AWS services with IAM Roles. IAM roles give access to the AWS services. Unlike IAM Users which are associated with the identity of the user, the IAM Roles are associated with the AWS Services.
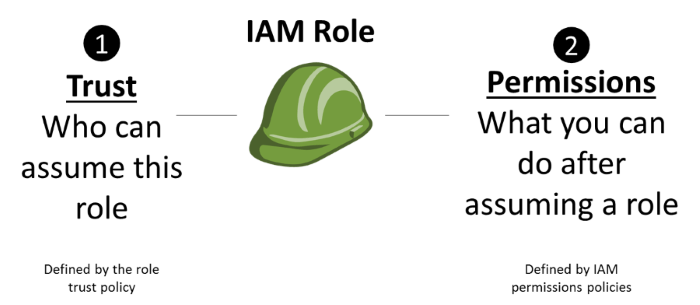
The IAM Roles are written in JSON files. A simple example of an IAM policy JSON file is:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::example-bucket/*"
},
{
"Effect": "Deny",
"Action": "s3:*",
"Resource": "*"
}
]
}
Version: It is generally used to specify the version of the policy language.
Statement: Statements are the series of permissions that are used to grant or deny permissions.
Effect: It specifies the Effect of applying the statement whether it allows or denies the action.
Action: It specifies the actions that are allowed or denied. In above example it allows "s3:GetObject" and denies all S3 actions (S3
:*).Resources: On which AWS Service the permissions are applied. in the above example, it is the S3 Bucket
EC2 Instance Roles:
When we launch an EC2 instance, we can specify an IAM role to be associated with the instance. Alternatively, we can associate or disassociate IAM roles with an existing EC2 instance at any time without having to stop or terminate the instance.

A simple example of EC2 roles for an EC2 Instance is below:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "ec2.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}
Lambda function Roles:
When we create a Lambda function, we specify an IAM role that AWS Lambda can assume to execute our function on our behalf. This role is assumed by the Lambda service, allowing the service to perform actions on other AWS resources during the execution of our function.

A simple example of Lambda function roles for a Lambda function is below:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "lambda.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}
IAM Security tools:
IAM Credential Report: A Report that lists all our account user and the status of their various credentials. It is an account-level Service.
IAM Access Advisor: Access advisor shows the service permission granted to a user and when the service was last accessed. It is a user-level Service.
IAM BEST PRACTICE
Don't use the root account expact for the AWS account setup.
One physical user = One AWS User.
Assign user to group and assign permission to group.
Creating a strong Password Policy.
Use and enforce the user of MFA.
Create and use roles for permitting AWS service
Use Access keys for Programmatic access [CLI/SDK].
Audit Permission of your account with the IAM Credential.
SHARED RESPONSIBILITY MODEL FOR IAM

| AWS | USER (WE) |
| Infrastructure [Global network security] | User, Group, Roles, Policies |
| Configuration and vulnerability analysis | Enable MFA on all account |
| Complaince validation | Rotate all your keys often |
| Use IAM tools to apply for appropriate permission | |
| Analyse access patterns and review permission |